Articles
Technical deep-dives into cybersecurity topics

Windows Access Tokens & Impersonation
In this article, we will dive into how Windows access tokens work and how they relate to SeImpersonatePrivilege exploitation.
Read more
Active Directory: Domain Trusts
Today, we'll delve into the fundamentals of Domain Trusts and how misconfigurations can be leveraged to achieve domain escalation/lateral movement.
Read more
Active Directory: Certificate Services (Part 2)
Today, we will delve into how Certificate Mapping works, which security measurements were implemented after the Certifried vulnerability and more.
Read more
Active Directory: Certificate Services (Part 1)
Today, we'll delve into Active Directory Certificate Services (ADCS). In this article, we'll cover fundamental concepts and later introduce exploitation techniques, as well as how to exploit them.
Read more
Active Directory: DACL Abuse
Today, we'll explore the exploitation of insecure ACEs within the DACL of users and groups in an Active Directory environment.
Read more
Active Directory: Windows ACLs
Today, we'll explore the fundamentals of ACLs in Windows and later demonstrate common attacks that exploit ACL misconfigurations in an Active Directory environment.
Read more
Active Directory: Attacking Kerberos
Today, we'll explore the exploitation of an AD environment, demonstrating how to carry out these attacks and apply the Kerberos Authentication Protocol in real-world exploitation scenarios.
Read more
Active Directory: Understanding Kerberos Authentication Protocol
In this article, we will dive into the theoretical foundations of Kerberos, explaining its core components, how the authentication process works.
Read more
Understanding the Heap: A Foundation for Advanced Exploitation
In this article, we explore the fundamentals of the heap as a stepping stone to understanding advanced memory corruption exploitation techniques.
Read more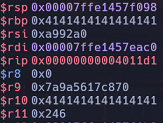
Buffer Overflow - Ret2libc (Part 2)
Today, we will continue exploring the Ret2libc technique, with a focus on 64-bit exploitation.
Read more
64-bit vs 32-bit
Up to this point, we have covered exploiting binary vulnerabilities in 32-bit programs. However, with the prevalence of 64-bit computing systems today, this article will introduce x64 binary exploitation.
Read more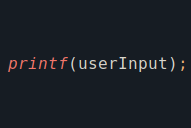
Format String Vulnerability
Today, we'll discuss a Binary Exploitation technique called Format String Vulnerability. We'll delve into how this vulnerability operates at a low level and explore how to exploit it to achieve memory overwrite.
Read more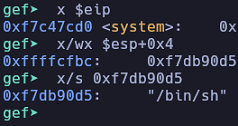
Buffer Overflow - Ret2libc (Part 1)
Today, we'll delve into the Return To Libc (ret2libc) technique and how we can take advantage of Libc to achieve code execution...
Read more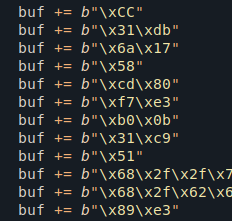
Buffer Overflow - Shellcode
Today, we'll delve into the Shellcode technique, focusing on exploiting buffer overflow to gain system access or potentially escalate privileges...
Read more
PLT & GOT: Key Players in Dynamic Linking
As a developer, you may have encountered these concepts and experienced how they interact with your programs. In this article, we'll delve into the Procedure Linkage Table (PLT) and the Global Offset Table (GOT).
Read more
Buffer Overflow - Introduction
What is a Buffer Overflow vulnerability? How can we achieve code execution by exploiting a Buffer Overflow? Today, we'll delve into various aspects related to Buffer Overflow vulnerabilities...
Read more
Binary Protections
What are binary protections? How do they prevent us from exploiting binaries? Today, we'll delve into these binary protections, exploring their purpose and how they function...
Read more
CPU & Assembly - Binary Exploitation Basics
Today, we'll delve into the fundamentals of the CPU, assembly language, memory, and how programs operate at a low level. This serves as a foundational knowledge for Binary Exploitation...
Read more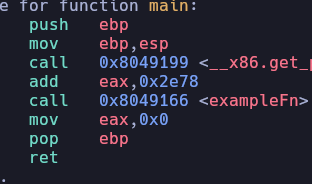
Assembly Instructions - Intel x86
For those who are not familiar with Assembly, I wrote this extra article which I'll explain Assembly Instructions in Intel x86 syntax, after reading this article, you can continue reading the Binary Exploitation basics.
Read more
Understanding Linux User IDs
In Linux, User IDs (UIDs) are unique numerical identifiers assigned to each user account on the system. These identifiers are used by the operating system to determine...
Read more